el bandido
TNAP-Images
For me personally, by far one of the best performances from Claude Code is this firewall, It will need to be tested on other receivers, but works nicely on the Octagon SF8008. The latest version (enigma2-plugin-security-firewall_1.0-r18_cortexa15hf-neon-vfpv4.ipk) Is not in the feeds or in a build. The firewall in OpenPLi feeds goes back a number of years, and probably around 2011 was the last working version. A lot of time and effort went into updating this plugin, mainly for my personal use, but also to be included in the TNAP builds.
Attached are two lengthy and perhaps at a point, boring documents about the efforts that went into this firewall, with at current count, 18 versions of the thing being made and rejected for one reason or another, or an improved version of the previous version. A lot of testing has gone into this firewall plugin, and it has been tested, proven to work as advertised. There can be no guarantee of individual results a user will have, and there is no such thing as a secure website or computer. But we do the best we can.
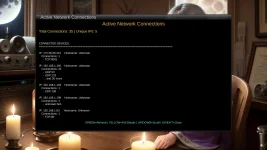
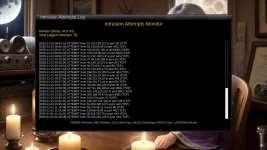
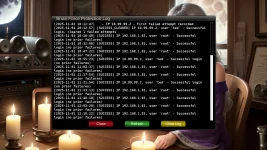
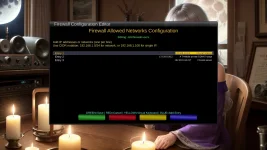
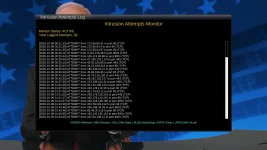
One file will need to be edited probably for each individual because each internet ip addresses will be expected to be different. Editing the file is easy, and can be done with Telnet, FTP, or plugins currently installed or available in TNAP images. The design of this firewall is simple: Let the few ip addresses through that the individual user needs, and block the rest! An onboard logger is also included. The logger shows the ip addresses of the attackers and also the port they were attacking.
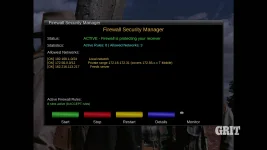
Note: This Firewall is Useless If It is Turned OFF!
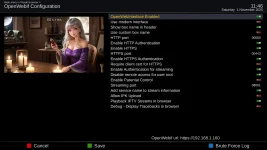
Do not depend on this firewall without checking it. If it is off, then you are subject to attackers. This firewall was updated and rebuilt to be used for streaming on the Internet using OpenWebif. It is but one piece of multi-layered security system. Using OpenWebif to stream over the Internet already requires a username and password. OpenWebif in TNAP was hardened a bit to discourage or confuse brute force attackers. A decent, long password should be considered for Internet streaming as that is your first line of defense, or last line of defense, depending on how you look at it.
Summaries from Claude Code are attached. They should be read in detail if you are considering the use of this firewall.
To be available in a future build, Revision r18 shown below.
Attached are two lengthy and perhaps at a point, boring documents about the efforts that went into this firewall, with at current count, 18 versions of the thing being made and rejected for one reason or another, or an improved version of the previous version. A lot of testing has gone into this firewall plugin, and it has been tested, proven to work as advertised. There can be no guarantee of individual results a user will have, and there is no such thing as a secure website or computer. But we do the best we can.
One file will need to be edited probably for each individual because each internet ip addresses will be expected to be different. Editing the file is easy, and can be done with Telnet, FTP, or plugins currently installed or available in TNAP images. The design of this firewall is simple: Let the few ip addresses through that the individual user needs, and block the rest! An onboard logger is also included. The logger shows the ip addresses of the attackers and also the port they were attacking.
Note: This Firewall is Useless If It is Turned OFF!
Do not depend on this firewall without checking it. If it is off, then you are subject to attackers. This firewall was updated and rebuilt to be used for streaming on the Internet using OpenWebif. It is but one piece of multi-layered security system. Using OpenWebif to stream over the Internet already requires a username and password. OpenWebif in TNAP was hardened a bit to discourage or confuse brute force attackers. A decent, long password should be considered for Internet streaming as that is your first line of defense, or last line of defense, depending on how you look at it.
Summaries from Claude Code are attached. They should be read in detail if you are considering the use of this firewall.
To be available in a future build, Revision r18 shown below.